24/04 – Weekly Fintech Recap
- 24.04.2023 09:00 am
11/11 – Weekly Fintech Recap
- 11.11.2022 06:00 pm
Equals Group Partners with Featurespace to Enhance...
- 22.08.2022 10:55 am
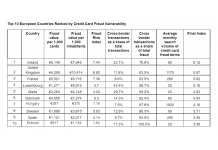
New Research Reveals Ireland is the Credit Card Fraud...
- 01.08.2022 09:50 am
18/07 – Weekly Fintech Recap
- 18.07.2022 09:00 am
Red Hat Releases Open Source StackRox to the Community
- 17.05.2022 01:25 pm
MSAB Part of New European Standard for Mobile Forensics
- 05.05.2022 09:20 am
Vyta Receives £11M Investment from MML and Acquires IT...
- 04.05.2022 11:10 am
MyComplianceOffice Announces Close of Schwab...
- 03.05.2022 01:00 pm
PSD2 and MFA - What Exactly Do They Mean?
- 08.02.2022 10:52 am
14/01 Weekly FinTech Recap – What’s the Hottest?
- 14.01.2022 08:00 am
DeFinity Partners with Leading Fintech Market...
- 22.12.2021 11:30 am